A new study has indicated that ‘100%’ of tested smartwatches exhibit security flaws, provides guidance for secure device use.
The study, from HP indicates that smartwatches with network and communication functionality represent a new and open frontier for cyberattack.
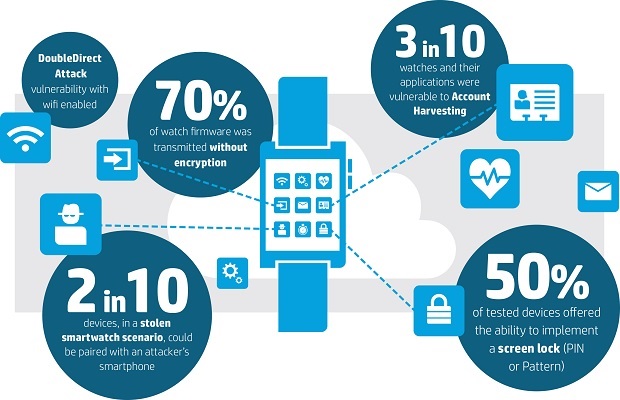
The study conducted by HP Fortify found that 100 percent of the tested smartwatches contain significant vulnerabilities, including insufficient authentication, lack of encryption and privacy concerns1. In the report HP provides actionable recommendations for secure smartwatch development and use, both at home and in the workplace.
As the IoT market advances, smartwatches are growing in popularity for their convenience and capabilities. As they become more mainstream, smartwatches will increasingly store more sensitive information such as health data, and through connectivity with mobile apps may soon enable physical access functions including unlocking cars and homes.
“Smartwatches have only just started to become a part of our lives, but they deliver a new level of functionality that could potentially open the door to new threats to sensitive information and activities,” said Jason Schmitt, general manager, HP Security, Fortify. “As the adoption of smartwatches accelerates, the platform will become vastly more attractive to those who would abuse that access, making it critical that we take precautions when transmitting personal data or connecting smartwatches into corporate networks.”
The HP study questions whether smartwatches are designed to store and protect the sensitive data and tasks for which they are built. HP leveraged HP Fortify on Demand to assess 10 smartwatches, along with their Android and iOS cloud and mobile application components, uncovering numerous security concerns.
The most common and easily addressable security issues reported include:
•Insufficient User Authentication/Authorization: Every smartwatch tested was paired with a mobile interface that lacked two-factor authentication and the ability to lock out accounts after 3-5 failed password attempts. Three in ten, 30 percent, were vulnerable to account harvesting, meaning an attacker could gain access to the device and data via a combination of weak password policy, lack of account lockout, and user enumeration.
•Lack of transport encryption: Transport encryption is critical given that personal information is being moved to multiple locations in the cloud. While 100 percent of the test products implemented transport encryption using SSL/TLS, 40 percent of the cloud connections continue to be vulnerable to the POODLE attack, allow the use of weak cyphers, or still used SSL v2.
•Insecure Interfaces: Thirty percent of the tested smartwatches used cloud-based web interfaces, all of which exhibited account enumeration concerns. In a separate test, 30 percent also exhibited account enumeration concerns with their mobile applications. This vulnerability enables hackers to identify valid user accounts through feedback received from reset password mechanisms.
•Insecure Software/Firmware: A full 70 percent of the smartwatches were found to have concerns with protection of firmware updates, including transmitting firmware updates without encryption and without encrypting the update files. However, many updates were signed to help prevent the installation of contaminated firmware. While malicious updates cannot be installed, lack of encryption allows the files to be downloaded and analyzed.
•Privacy Concerns: All smartwatches collected some form of personal information, such as name, address, date of birth, weight, gender, heart rate and other health information. Given the account enumeration issues and use of weak passwords on some products, exposure of this personal information is a concern.
As manufacturers work to incorporate necessary security measures into smartwatches, consumers are urged to consider security when choosing to use a smartwatch. It’s recommended that users do not enable sensitive access control functions such as car or home access unless strong authorization is offered. In addition, enabling passcode functionality, ensuring strong passwords and instituting two-factor authentication will help prevent unauthorized access to data. These security measures are not only important to protecting personal data, but are critical as smartwatches are introduced to the workplace and connected to corporate networks.
Matt White, Senior Manager in KPMG’s cyber security practice commented on new research by HP on smartwatch security: “With the high profile release of smart watches in recent months, it was inevitable that security flaws were identified. As is often the case, consumer demand for new and exciting technologies have far surpassed the implementation of security measures.
“Many of the watches (and other wearable technologies) use ‘device pairing’ along with pin/password to provide authentication, but this alone provides limited protection form a serious assailant. As with many security conversations, the level of security is a recipe of convenience, user experience and security.
“The final ingredient is the level of awareness of the end user. It would be a fair assumption that for the average consumer the general level of awareness is low, but this begs the question of who should be responsible for the protection of them? Should it be the manufacturer or the user themselves? The answer isn’t clear, but it’s likely that the ‘bad guys’ won’t be waiting for security to catch up with the current advancements.”
Additional guidelines for secure smartwatch use are outlined in the full report.
Methodology
Conducted by HP Fortify, the HP Smartwatch Security Study used the HP Fortify on Demand IoT testing methodology which combined manual testing along with the use of automated tools. Devices and their components were assessed based on the OWASP Internet of Things Top 10 and the specific vulnerabilities associated with each top 10 category.